If you are reading this on a Windows device, you need to watch out for dangerous new malware that has been infecting internet browsers, password managers, and even cryptocurrency wallets. The Uptycs Threat Research team has named the malware “The Meduza Stealer” after Meduza, the threat actor who created it. Although no specific attacks have been attributed to The Meduza Stealer yet, Uptycs says the malware is capable of “comprehensive data theft.”
Uptycs says that the administrator of The Meduza Stealer has been promoting the new malware by showing that it can successfully evade detection by reputable antivirus software. Screenshots show Bitdefender, AVG, Kaspersky, and McAfee all failing to detect the malware in static and dynamic scans of the Meduza stealer file:
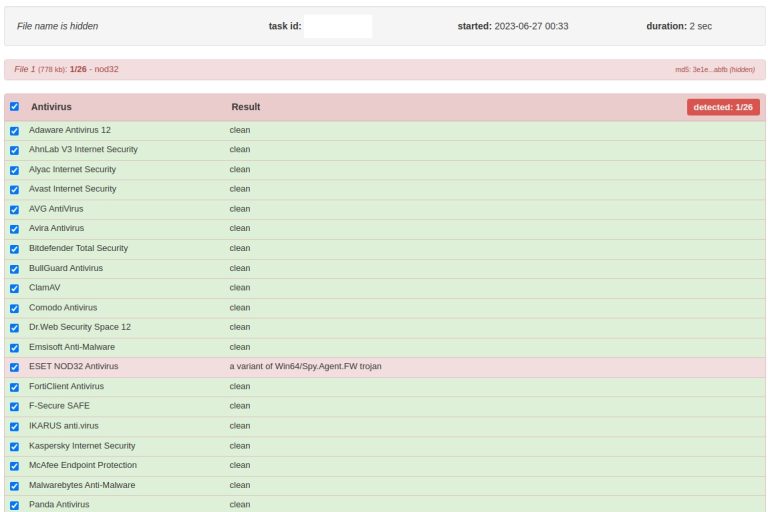
UPDATE 7/13: We previously included Malwarebytes on the list above, but the company reached out to let us know that its software does detect and block this malware and has since mid-June.
Here’s how the malware actually works once it infiltrates your computer:
The first step it performs is a geolocation check. If the victim’s location is in the stealer’s predefined list of excluded countries, the malware operation is immediately aborted. However, if the location isn’t on the list, Meduza Stealer checks if the attacker’s server is active. In case the server isn’t accessible, the stealer also promptly terminates its activity. If both conditions—location check and server accessibility—are favorable, the stealer proceeds to gather extensive information. This includes collecting system information, browser data, password manager details, mining-related registry information, and details about installed games. Once this comprehensive set of data is gathered, it is packaged and uploaded, ready to be dispatched to the attacker’s server, thereby completing the stealer’s operation within the infected machine.
As noted above, the malware targets several sensitive apps, including browsers and password managers. The list of browsers The Meduza Stealer attacks include several versions of Chrome, Edge, Firefox, Opera, Brave, and dozens more I’ve never even heard of.
Other noted targets include the Steam software client, Discord, password managers, two-factor authentication apps, and cryptocurrency wallet extensions.
In order to avoid becoming a victim of The Meduza Stealer malware, Uptycs recommends you regularly install updates for your computer and any applications, be careful when downloading files, use strong passwords, and avoid suspicious browser extensions.








